What is cyber risk and why is it key to implementing ISO 27001?
In the digital world, cyber risk is no longer just a buzzword - it's a critical business issue. An accurate understanding of cyber risk is essential for the development of an Information Security Management System (ISMS), especially when implementing ISO/IEC 27001.
But what exactly is cyber risk and how is it composed?
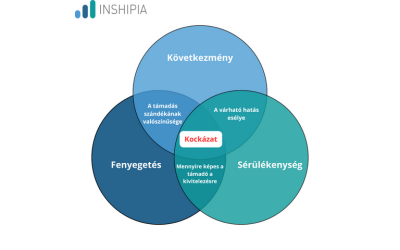
Three pillars of cyber risk:
1. Threat
The actor or event that could cause harm - for example, hackers, ransomware, phishing attacks.
What affects it?
The attacker's intent
The ability of the attacker
2. Vulnerability
A weakness in your system that the threat could exploit - for example, outdated software, incorrectly set permissions.
3. Consequence
The actual damage or impact that occurs when a threat successfully exploits a vulnerability - for example, loss of data, business downtime, legal consequences.
This determines the likelihood of impact.
How do we manage risks?
- Reducing vulnerabilities
- Anticipating and averting threats
- Minimise consequences (e.g. backups, business continuity)
ISO 27001 aims precisely to provide a system-wide approach to these challenges. A well-implemented ISMS not only promotes compliance, but also enhances a company's security, reputation and customer confidence.

